User Administration
Introduction
The SR 1.3 – Account management cybersecurity requirement states that the control system shall provide the capability to support the management of all accounts by authorized users, including adding, activating, modifying, disabling and removing accounts.
That means after delivering the CDP System to the end customer, they will need to be able to manage the user accounts.
Every fresh CDP System has 5 roles predefined:
| Role | Description |
|---|---|
| ConfigureAdmin | By default allows to view, change and add/remove everything but permissions |
| SecurityAdmin | Allows to change permissions and manage every other user in the system (including add/remove) |
| EndUserAdmin | Intended to manage (including add/remove) all users except system provider made users (those having ConfigureAdmin or SecurityAdmin role) |
| Operator | By default allows to view and change everything (but no add/remove) |
| Observer | By default allows to view everything |
The purpose of this tutorial is to describe how to set up the EndUserAdmin role to create a special administrator account that can add, remove and manage other user accounts except for some special high-privileged users created by the system provider that have the rights to develop and update the system.
Glossary
- End user account - an account meant to be used by the customer for day-to-day operations after the system is delivered. These accounts should be managed by the EndUserAdmin role.
- System provider account - an account meant to be used by the developer or the provider of the system to add extra functionality, configure the system or install updates. The EndUserAdmin should not be able to disable these accounts.
Note: While in this example the EndUserAdmin cannot manage system provider accounts, this is just an example. Using the same principles, it is possible to set up permissions in a different way.
Setting up User Accounts
To set up users and authentication, open your system in CDP Studio and go to the Security tab ().
Note: A much more detailed description of the Security tab and all its features is available in the Security Manual.
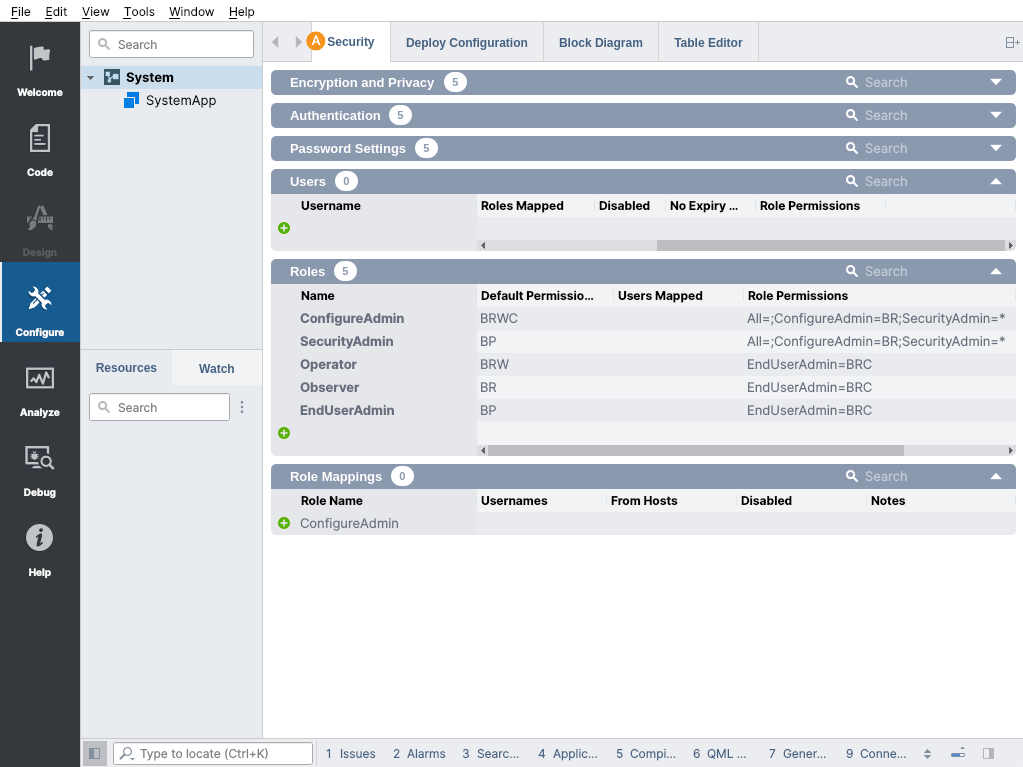
Next, add some user accounts (). In this example, we will be creating four of them.
Note: The following usernames are only an example. In real systems, a user account should be created for each individual person so that different people would not share passwords.
| User | Description |
|---|---|
| Admin | The admin account given to the end user that can add, remove and manage Operator and Observer accounts. |
| Security | This account has the SecurityAdmin role. It has full access to edit the permissions of any end user or system provider account. |
| Dev | Intended to be used by the developer or the provider of the system to add extra functionality, configure the system or install updates. It has the ConfigureAdmin role. |
Note: After adding the user accounts, remember to configure the initial password using the Set Password button in the Users table.
Then add the role mappings () and finally, fill the Usernames column to tie the roles with the users () as shown in the picture below.
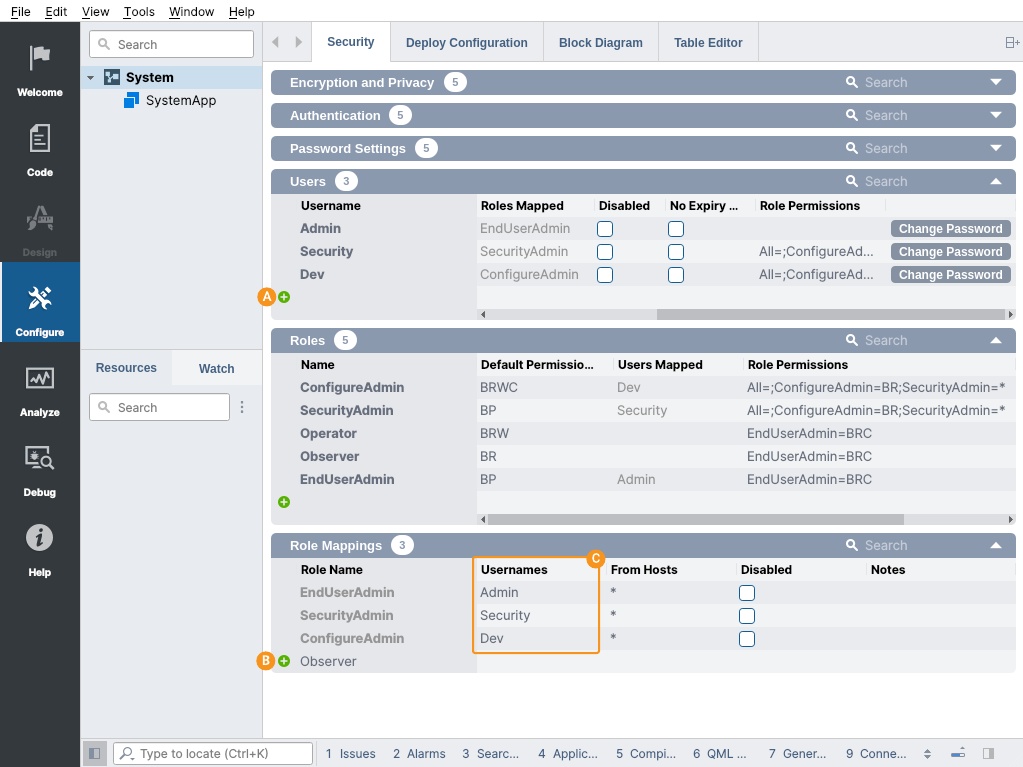
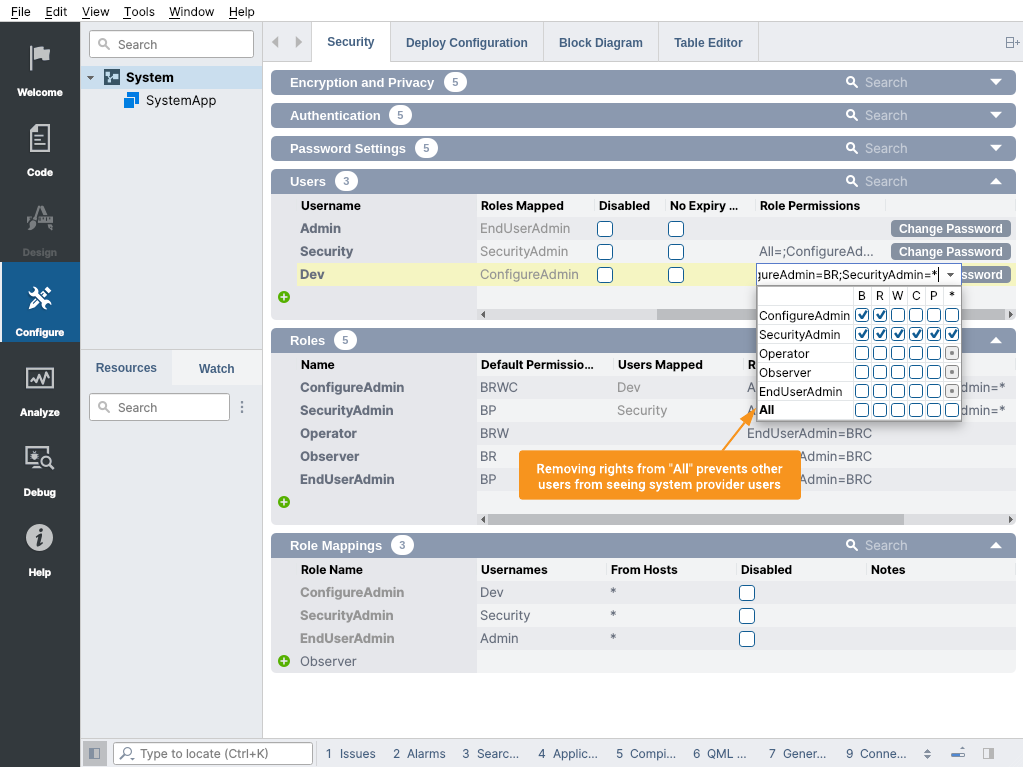
After adding the users, by default the EndUserAdmin has access to all of them. However, in this example we want the system provider users Security and Dev to not be visible to end user accounts. For that edit the Role Permissions column of the Users table and disable the access for All and give special access to the Security and Dev users as displayed in the image below.
Now the system should be configured and ready for testing.
- Run & Connect the system and log in with the Admin user. If done correctly, only the Admin account should be visible in the Users table.
- Next, add a new user account named User with the button (). Notice that by default the EndUserAdmin that added the user has full access to it (). Configure the initial password using the Set Password button.
- Add a role mapping for Operator with the button ().
- Finally, add the new user to the Usernames list for the Operator role mapping ().
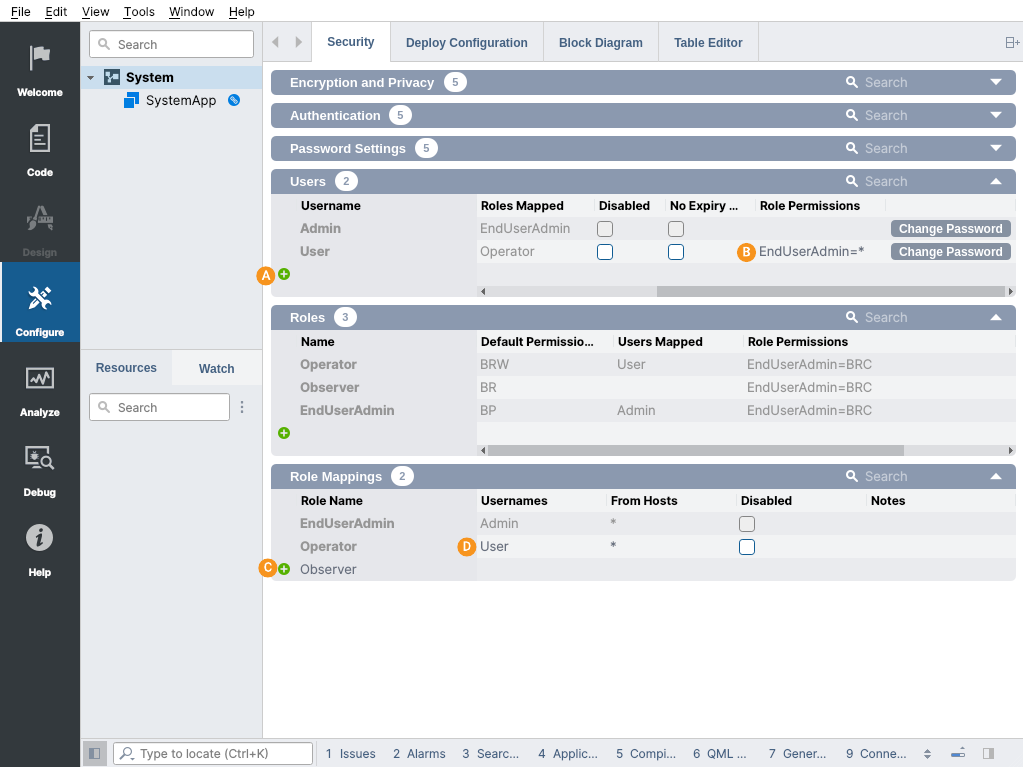
Now the system has a new end user named User with the Operator role which allows to view and edit any value in the system.
Note: If we had added the new User before clicking Run & Connect and logging in with the Admin user, we would have had to manually add the "EndUserAdmin=*" Role Permission to the new user account to specify that this is an end user account.
Security Configurator Tool Web UI
The end user should not be expected to install CDP Studio to manage user accounts. For that it is recommended to deploy the Security Configurator Web UI with the system.
Get started with CDP Studio today
Let us help you take your great ideas and turn them into the products your customer will love.