Linux Realtime Configuration
About
This page describes how to configure Linux to allow realtime processes for a user, or how to use setcap to grant specific permissions for an executable.
CDP Studio includes functionality for easily setting this up as explained in the App Manager documentation.
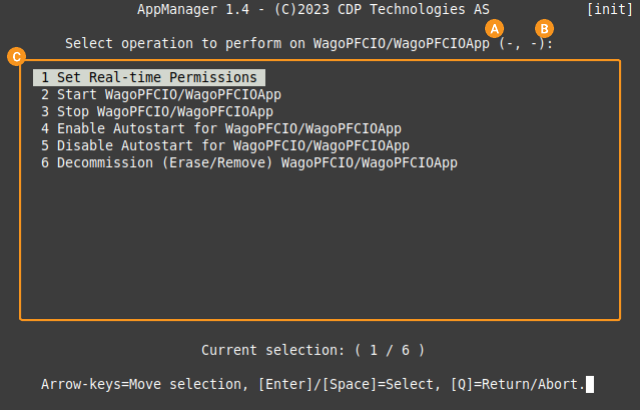
For cases where this can not be used, the documentation below explains how to set this up manually.
Using setcap
The recommended approach, if the operating system supports it and the user has the correct access rights, is to use setcap to grant permissions to an executable. The typical syntax is
setcap "cap_net_bind_service,cap_net_admin,cap_net_raw,cap_sys_boot,cap_sys_nice,cap_sys_time+ep" "/path/to/app_name"
Note: Whenever your application is deployed, you have to run setcap again!
Take care to only set the minimum amount of required options. For more information about setcap options, see the setcap capabilities man-page.
Editing limits.conf
Instead of setting permissions on the executable using setcap, it is possible to set up permissions for a user by editing /etc/security/limits.conf.
Note: The changes to the permissions grants the user capabilities to run real-time processes and disallow paging large blocks, and is dangerous from a security perspective. Make sure to do a risk evaluation, secure the operating system by following industry best practices, and by segregating the system into zones and conduits to reduce the risk this introduces. Adjust limits.conf as required. For more information, see the Cybersecurity Requirements.
The example is assuming we want to set up a Raspberry Pi. Make sure that the Raspberry Pi is Paired.
- Log into the Raspberry Pi by right-clicking the Paired device in the Configure mode Deploy Configuration Devices table, and open a remote shell as described in Manually Running Scripts and Commands on a Remote Device.
- Edit the file /etc/security/limits.conf using 'nano':
sudo nano /etc/security/limits.conf
- Using the arrow-keys, move the cursor to the line before
# End of file - ... And copy and paste the following text:
pi - rtprio 99 pi - memlock unlimited pi - nice -20
- Press the Ctrl+x keys, and type 'y', then press Enter to exit the 'nano' editor.
- The target must be rebooted for the change to take effect. To reboot the target, type:
sudo reboot
This will stop all running processes, power off the target and power it back on.
Get started with CDP Studio today
Let us help you take your great ideas and turn them into the products your customer will love.