LDAP Authentication Method
LDAP Authentication Method
With this method, the users will be authenticated by an external LDAP server. This method can be used in any CDP application (e.g. Console, GUI or WebUI), to replace or be in parallel with other methods, like the default password-based authentication.
With this method, the user's credentials will be verified using an external LDAP such as OpenLDAP, Microsoft Active Directory or any other LDAP server that supports the LDAP version 3 (or newer) protocol.
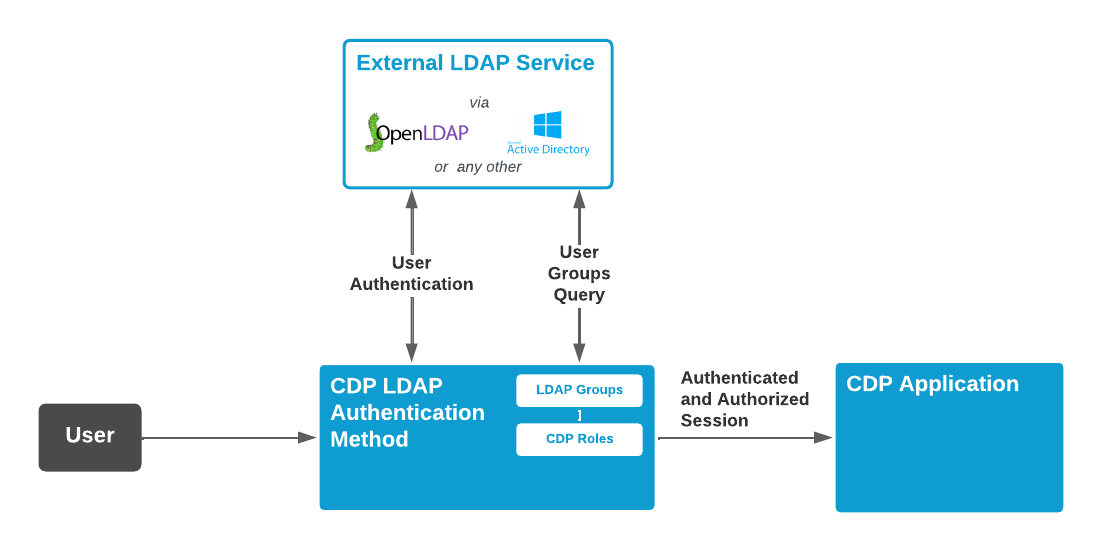
To ease up user management, with the LDAP authentication method the user does not have to pre-exist in the CDP Security database. If the user does not exist in the CDP Security database, the user entry will be created after successful LDAP authentication with CDP roles corresponding to the user LDAP groups. In other words, all LDAP users that have the configured LDAP group(s) assigned will be able to log in to the CDP application without the need to create the user or set an initial password for the user in the CDP.
To add the method, select the LDAP from the bottom row Type column and click on the in front of the row or drag the LDAP Authentication resource from the Resource tree to the Authentication Methods table. To edit the method properties, click the navigate button in front of the method name and the editing window opens up.
This method has the following configurable properties:
| Setting | Description |
|---|---|
| ServerHost | LDAP server host address |
| ServerPort | LDAP server port. Usual values are 389 when Encryption is set to Unencrypted or StartTLS and 636 when Encryption is set to TLS. |
| BindDN | LDAP user bind DN string. %s will be replaced with the entered username on bind. |
| Timeout | Timeout to wait for LDAP requests |
| AutoCreateCDPUser | When set, the LDAP authenticated user does not have to pre-exist in the CDP Security database - then it will be created after successful LDAP authentication and with CDP roles matched via LDAPGroupRoleMapping-s assigned. |
| Encryption | LDAP server connection encryption. Options are Unencrypted, TLS, and StartTLS. Should use TLS or StartTLS whenever possible to prevent credential leakage over communication channel with LDAP server. |
| TLSMinVersion | Minimum TLS version that is allowed for LDAP server TLS connection. Options are TLSv1.1, TLSv1.2, and TLSv1.3. |
| TLSServerCACertFile | LDAP server host certificate issuer (CA) file name (for TLS certificate-based broker verification) |
| TLSClientCertFile | Optional LDAP client authentication certificate file name (for TLS client authentication) |
| TLSClientKeyFile | Optional LDAP client authentication key file name (for TLS client authentication) |
| TLSAllowVerificationErrors | Allow verification errors in the TLS connection |
| LDAPLogLevel | Logging flags of the LDAP backend library, set to -1 to enable all types |
The LDAP authentication method also has a list of LDAPGroupRoleMapping elements, which can be added to configure how to map LDAP groups to CDP roles. The LDAPGroupRoleMapping can be added by clicking the in front of the LDAPGroupRoleMapping property or by dragging the LDAPGroupRoleMapping resource from the Resource tree to the LDAP Authentication method editing window.
Note: The LDAPGroupRoleMapping is only used when the user has no roles configured in the CDP Security database. For users who already have roles configured in the CDP Security database, the LDAPGroupRoleMapping is not applied.
For the LDAPGroupRoleMapping, the following properties can be configured:
| Property | Description |
|---|---|
| GroupDN | LDAP group full DN |
| Roles | Semicolon-separated list of Roles to map to that LDAP group |
| Disabled | Can be used to disable this mapping temporarily |
| Notes | Admin notes for the mapping |
Note: Every user must have at least one role assigned to be able to log in.
Password and LDAP Authentication
When both password and LDAP authentication methods are enabled, the user can log in with either method. The methods are tried in the order they are listed in the Authentication Methods table, from top to bottom.
When you move the Password authentication method to the bottom of the list, the LDAP authentication method will be used first, and password authentication only when there is a problem with LDAP authentication. This way, you make the LDAP authentication method to be the primary authentication method and the password authentication method as a fallback method.
Get started with CDP Studio today
Let us help you take your great ideas and turn them into the products your customer will love.