How To Set Up Google Authentication Using HTTP Reverse Proxy
How To Set Up Google Authentication Using HTTP Reverse Proxy
This guide describes how to set up an external HTTP reverse proxy for user authentication via Google by using either Apache or NGNIX web server.
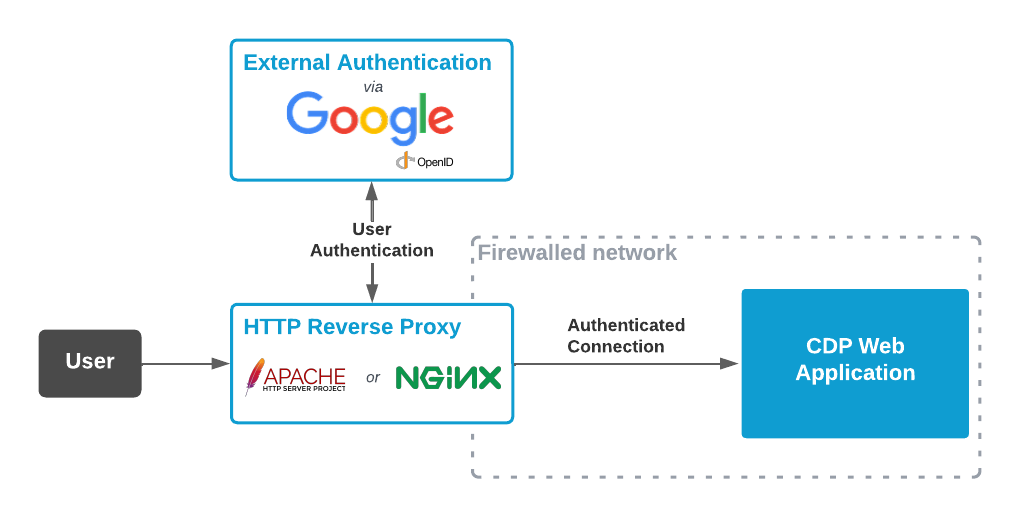
CDP web applications can be authenticated via the external HTTP authentication proxy as described in Reverse HTTP Proxy Authentication Method documentation.
This tutorial describes how to configure Apache or NGNIX web servers as authentication proxies so that users can log into CDP web application using their Google account (using Google OpenID Connect authentication service).
Configure CDP Application In Google API Console
To add Google authentication support to the CDP application, the Google API developer backend has first to be configured to enable this CDP application authentication. For that, follow the steps below:
- Log to the Google API Console https://console.developers.google.com/
- Select or create a project
- Click on the "Credentials" tab on the left-hand side menu
- Click on the "+ Create Credentials" button and select "OAuth client ID"
- Choose "Web Application"
- Enter the required information, such as:
- The name of the CDP application
- The authorized JavaScript origins: reverse HTTP proxy listen address (or list of addresses), that the end users will use when they start logging into the CDP application. By this security setting Google can deny any authentication tries from any other addresses for that application.
- The authorized redirect URIs: reverse HTTP proxy redirect (callback) address Google will redirect the user back when the user is authenticated. Must start with the JavaScript origin URI suffixed to some string, like /redirect_uri. This URI must not point to any actual address or resource on the web server. The URI must match the address configured as a redirect URI in the proxy configuration (see below).
- Click on the "Create" button
- Copy and save the generated and displayed Client ID and Client secret as they will be needed in the proxy configuration (see below).
Set Up CDP security
To enable reverse HTTP proxy authentication with Goole authentication in CDP:
- Open CDP Security Configuration editor
- From last row of Authentication Methods choose Type ProxyAuthentication and click "+" button in front of the row, to add the method
- Click the navigate button in front of the added method name
- In the editor opened, set UsernameHeader to X-Forwarded-User and HostHeader to X-Forwarded-For
- For additional security, set the EnabledFrom to the proxy (internal) IP address
Configure Apache Web Server as HTTP Reverse Proxy With Google Authentication
To configure the Apache web server for reverse proxy with Google OIDC authentication, follow these steps:
Install and enable the required Apache with modules: mod_proxy, mod_proxy_http, mod_proxy_wstunnel, mod_auth_openidc and mod_headers. The following Linux command can be used to install it and enable these modules:
sudo apt install apache2 sudo apt install libapache2-mod-auth-openidc sudo a2enmod ssl proxy proxy_http proxy_wstunnel rewrite auth_openidc headers sudo a2ensite default-ssl
Then configure Apache as a reverse proxy by editing the configuration file of the virtual host. For example, add lines like below to the default Apache SSL site configuration file (/etc/apache2/sites-enabled/default-ssl.conf), into the VirtualHost section:
<IfModule mod_ssl.c> <VirtualHost _default_:443> ... ProxyRequests Off SSLProxyEngine on SSLProxyCheckPeerCN off OIDCProviderMetadataURL https://accounts.google.com/.well-known/openid-configuration # In the following line, replace the XXX with the ClientID copied from Google API Console: OIDCClientID XXX # In the following line, replace the YYY with the Client Secret copied from Google API Console: OIDCClientSecret YYY # In the following line, replace the URI with the redirect URI configured in the Google API Console: OIDCRedirectURI http://localhost/redirect_uri # Mandatory internal password for crypto purposes, this is used for: # - encryption of the (temporary) state cookie # - encryption of cache entries, that may include the session cookie, see also: OIDCCacheEncrypt and OIDCSessionType # If the value begins with exec: the resulting command will be executed and the first line returned to standard output # by the program will be used as the password OIDCCryptoPassphrase "exec:/bin/bash -c \"head /dev/urandom | tr -dc A-Za-z0-9 | head -c 32\"" OIDCScope "openid email" RewriteEngine on RewriteCond %{HTTP:Authorization} . RewriteRule .* - [E=HTTP_AUTHORIZATION:%{HTTP:Authorization}] RewriteCond %{HTTP:Upgrade} websocket [NC] RewriteCond %{HTTP:Connection} upgrade [NC] # In the following line, replace the URI with the actual URI of the CDP Application: RewriteRule ^/?(.*) "wss://localhost:7689/$1" [P,L] <Location /> AuthType openid-connect Require valid-user RequestHeader set X-Forwarded-User %{OIDC_CLAIM_email}e # In the following 2 lines, replace the URI with the actual URI of the CDP Application: ProxyPass https://localhost:7689/ ProxyPassReverse https://localhost:7689/ </Location> </VirtualHost> </IfModule>
Short description of the above configuration:
- The mod_auth_openidc module is configured to authenticate users with Google OIDC. Replace the OIDCClientID, OIDCClientSecret and OIDCRedirectURI values, as described in the comment lines
- The ProxyPass, ProxyPassReverse and Rewrite directives are used to forward all other requests to the CDP StudioAPI server (replace the addresses to be the actual CDP application server address)
- By RequestHeader directive the authenticated user's email address will be set as an HTTP header (X-Forwarded-User) and will be forwarded to the CDP application StudioAPI server
Now apply the configuration changes to the Apache server. The following Linux command can be used to apply them:
systemctl restart apache2
Note: Above are the very minimum configuration settings needed to get the authentication working. However, there are many other important configuration settings in the module, that should be reviewed and tuned accordingly, for advanced security. See the https://github.com/OpenIDC/mod_auth_openidc for more information about them. Also, a dedicated TLS key-pair and certificate matching the proxy hostname and signed by some valid CA should be created and set up in Apache mod_ssl configuration for warning-less usage for users in the browsers (as this example configuration is using the default insecure self-signed TLS certificate generated at the Apache installation). See the https://httpd.apache.org/docs/current/en/mod/mod_ssl.html for more information.
Configure NGNIX Server as HTTP Reverse Proxy With Google Authentication
Alternatively, the NGINX web server can be configured as a reverse proxy with Google OIDC authentication. To configure NGINX (OpenResty version of the server, that has a free Google OIDC authentication module available), follow these steps:
Install NGINX OpenResty version as described at https://openresty.org/en/installation.html
Install lua-resty-openidc module. This can be installed with Luarocks LUA package manager using these Linux commands:
sudo apt install luarocks sudo luarocks install lua-resty-openidc
Then configure NGINX OpenResty as a reverse proxy by editing the configuration file. For example, add lines like below to the default NGINX configuration file (/usr/local/openresty/nginx/conf/nginx.conf), into the http and location / sections:
http {
...
map $http_upgrade $connection_upgrade {
default upgrade;
'' close;
}
lua_package_path "/usr/local/share/lua/5.1/resty/*.lua;;";
resolver 8.8.8.8;
lua_ssl_trusted_certificate /etc/ssl/certs/ca-certificates.crt;
lua_ssl_verify_depth 5;
# cache for discovery metadata documents
lua_shared_dict discovery 1m;
# cache for JWKs
lua_shared_dict jwks 1m;
server {
...
location / {
# Use lua-resty-openidc to authenticate with Google OIDC
access_by_lua_block {
local opts = {
-- Specify Google OIDC discovery URL
discovery = "https://accounts.google.com/.well-known/openid-configuration",
-- In the following line, replace the XXX with the ClientID copied from Google API Console:
client_id = "XXX",
-- In the following line, replace the YYY with the Client Secret copied from Google API Console:
client_secret = "YYY",
-- In the following line, replace the URI with the redirect URI configured in the Google API Console:
redirect_uri = "http://localhost/redirect_uri",
-- Path to redirect the user for logout
logout_path = "/logout",
}
-- Call authenticate function with options
local res, err = require("resty.openidc").authenticate(opts)
-- Check for errors
if err then
ngx.status = 500
ngx.say(err)
ngx.exit(ngx.HTTP_INTERNAL_SERVER_ERROR)
end
-- Set email header from user info claim
ngx.req.set_header("X-Forwarded-User", res.user.email)
}
# In the following line, replace the URI with the actual URI of the CDP Application:
proxy_pass http://localhost:7689/;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection $connection_upgrade;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
}
...
}
Short description of the above configuration:
- The lua-resty-openidc module is used to authenticate users using Google OIDC. Replace the client_id, client_secret, redirect_uri as described in the comment lines
- The proxy directives are used to forward all other requests to the CDP StudioAPI server (replace the address to be the actual CDP application server address)
- By ngx.req.set_header directive the authenticated user's email address will be set as an HTTP header (X-Forwarded-User) and will be forwarded to the CDP application StudioAPI server
Now apply the configuration changes to the NGINX server. The following Linux command can be used to apply them:
systemctl restart nginx
Note: Above are the very minimum configuration settings needed to get the authentication working. However, there are many other important configuration settings in the module, that should be reviewed and tuned accordingly, for advanced security. See the https://github.com/zmartzone/lua-resty-openidc for more information about them.
Users Setup
With the above configuration, an authenticated user Google e-mail is forwarded to CDP as an authenticated user id. Because of that, for CDP to be able to authorize users in CDP, all users (that have to be able to log in using Google) have to be configured by setting their Google e-mail address as the Username in Security Configuration. Also, roles have to be assigned to these users according to their needs and duties, as usual.
Note: No password has to be set for the users in the CDP Security Configuration. But, it may be useful to set the password for (some) users - then they will be able to connect to the system also without external authentication available (like from the local network, for example using CDP Studio).
Reauthentication and Logout
Using the proxy authentication via Google, once the user is successfully authenticated the session will remain valid and the user can re-open the applications without re-authentication needed. However, re-authentication will happen when:
- the Google authentication session is expired (that can take several days, depending on the Google account settings)
- user has been explicitly logged out from Google SSO (for example going to address https://myaccount.google.com and choosing "Sign Out").
- the user has explicitly clicked the logout URL (for example to the URL OIDCRedirectURI with parameter ?logout=get for Apache module or to the URL {logout_path} for NGINX module). Inspect the module documentation for more information about logout and its configuration.
Get started with CDP Studio today
Let us help you take your great ideas and turn them into the products your customer will love.